简述
1 | pid=$(pgrep ranker_service) |
dump
1 | gdb bin/ranker_service core.9085 |
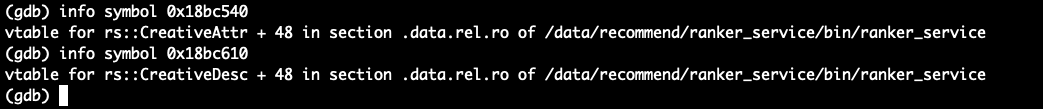
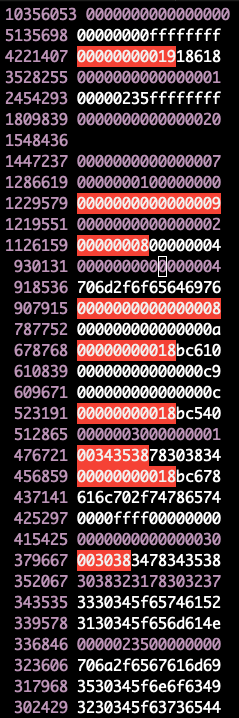
统计 vtable
1 | hexdump result.bin | awk '{printf "%s%s%s%s\n%s%s%s%s\n", $5,$4,$3,$2,$9,$8,$7,$6}' | sort | uniq -c | sort -nr > hex.t |
1 | pid=$(pgrep ranker_service) |
dump
1 | gdb bin/ranker_service core.9085 |
统计 vtable
1 | hexdump result.bin | awk '{printf "%s%s%s%s\n%s%s%s%s\n", $5,$4,$3,$2,$9,$8,$7,$6}' | sort | uniq -c | sort -nr > hex.t |

